Development of Cyber-pi
Cyber-pi helps SMEs to comply with GDPR and to protect personal and sensitive data they keep from attacks on privacy.
An evaluation on sources and models of distribution of cyber intelligence will be conducted.
Dependency on self-healing models for system recovery from cyber attacks and reliance upon technologies of Tessera corporation for the visualization of intelligence.
In the context of the proposed research the aforementioned models will be expanded by embedding the requirements of privacy and adaptive intelligence with semantic characteristics based on existing models and formats (STIX2, SIGMA).
Finally, Open Source SIEM (Security Incident Management System) Software OSSEC will be utilized. InnoSec has contributed to the development of this software.
Project Objectives
Timely detection and effective treatment of attacks against privacy of natural persons and protection of personal and sensitive data from disclosure, comprise a core demand of citizens as well as a legal obligation of organizations which collect and process personal data.
Recent data show that digital threats are evolving rapidly: from the dawn of 2016 more than 4000 attacks take place each day. This number is increased by 300% compared to 2015. Meanwhile, last year 80% of the European businesses were affected. Surveys show that financial repercussions of cybercrime have increased five-fold between 2013 and 2017 and that this number is subject to increase by four times until 2019.
More than half of cyber attacks target SMEs while 32% of these enterprises discovered security breaches the last year with an indicative cost that exceeds 4000 euros for very small enterprises. In addition, SMEs and organizations, despite the increase of attacks, lack the investment in security mechanisms and personnel although they understand their obligation to comply with GDPR and protect personal data that they have in their possession. On the other hand, existing services and products for breach monitoring and management (SIEM) refer to a market that will approach 6.75 billion dollars but their solutions are too expensive for SMEs because they do not focus solely on the protection of privacy and they do not take into account the specific business functions, their personnel or their technological environment. The precious findings define the starting point for the inception and development of Cyber-pi which comes to fortify SMEs from cyberattacks that can expose their digital data. Produced research will follow this direction and it will provide innovative characteristics to the product rendering it extremely competitive in the NextGen SIEMs market.
A Unified Intelligent Privacy Breach Management System
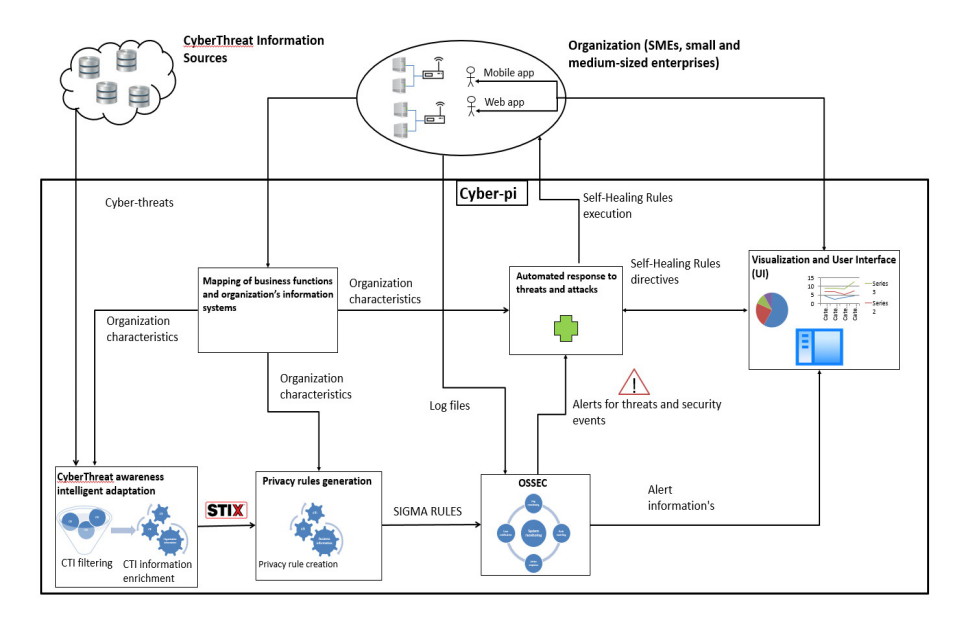
Development of a mechanism for gathering intelligent cyber knowledge (IOC, RSS etc) from trustworthy sources (e.g. MISP, Hail-a-TAXII) and the extension of it with semantic properties in line with the specific characteristics of each organization (technological environment, objective, geographical position, dependencies etc). In addition, it will distribute the adapted cybernetics to the STIX 2.0 standard.
Development of a methodology for matching the business functions and the specific characteristics of an organization (technological environment, staff etc) with a SIEM supporting automated production of rules based on SIGMA language with the objective of detecting privacy breaches. This methodology will take into account the targeted cyber threat intelligence which will be produced from the Cyber Threat Intelligence Smart Adaptation Subsystem.
Development of an intelligent system for the adaptive presentation of alarm notifications regarding privacy breaches as well as the overall status through a console (dashboard), satisfying the requirements for intelligent briefing (e.g. alert categorization) and approval by different users (user experience).
InnoSec’s existing research will be expanded to include features for systems interoperability with the objective of reducing and deterring attacks on privacy.
Pilot Application Scenarios
- The first scenario involves an enterprise with significant risks of attacks on privacy which possesses security mechanisms and personnel.
- The second scenario involves a small company without any security infrastructure and without specialized personnel but with exposure to attacks on privacy.
In the following schema the basic architecture of Cyber-pi, data flows and the dependencies if its subsystems are presented.
Conditions for the successful implementation and completion of this Research
The two partners of the joint venture maintain a great level of cooperation and they have successfully worked together in the past, claiming and realizing funded research (HORIZON, FIWARE) and other professional projects.
- They maintain remarkable infrastructure and high caliber affiliate researchers with significant researching experience.
- The mitigation of any failures in the schedule and objectives of the proposed research is ensured through the organizational structure and project management.
- Finally, among the body of researchers that participate in the project, is the distinguished scientist in Systems Security Prof. Katos V. of Bournemouth University (UK), founder and director of BU-CERT (UK), who will contribute to the evaluation and internationalization of Cyber-pi.
Project Implementation Methodology
The implementation methodology that will be followed is mainly bibliographical and secondarily experimental. Through the course of the project all of the State of the Art methods regarding data security and privacy will be studied. The system under development, implementing experimental methodologies, will be adapted to the needs of SMEs with the ultimate objective being the development of the release product.
In the initial stage of the methodology the basic roles and responsibilities of those in charge, as it is indicated by the organizational structure of the project, will be defined. By the integrating the project to the methodology, its structure with be further analyzed and imprinted according to the phases.
More specifically, WP1 has the target of evaluating the current technological research, the modeling of the characteristics of businesses or organizations, the design of the system architecture and the development of a plan to capitalize on the produced research. WP2 focuses on the development of the Cyber Threat Intelligence Smart Adaptation Subsystem. To this end, it collects cyber threat intelligence from relevant sources and it adapts it to each organization depending on its specific characteristics.
WP3 focuses on the development of Automated Privacy Rules Production Subsystem for the detection mechanism to use based on Smart Adaptation Cyber Threat Intelligence produced by the corresponding subsystem in WP2.




