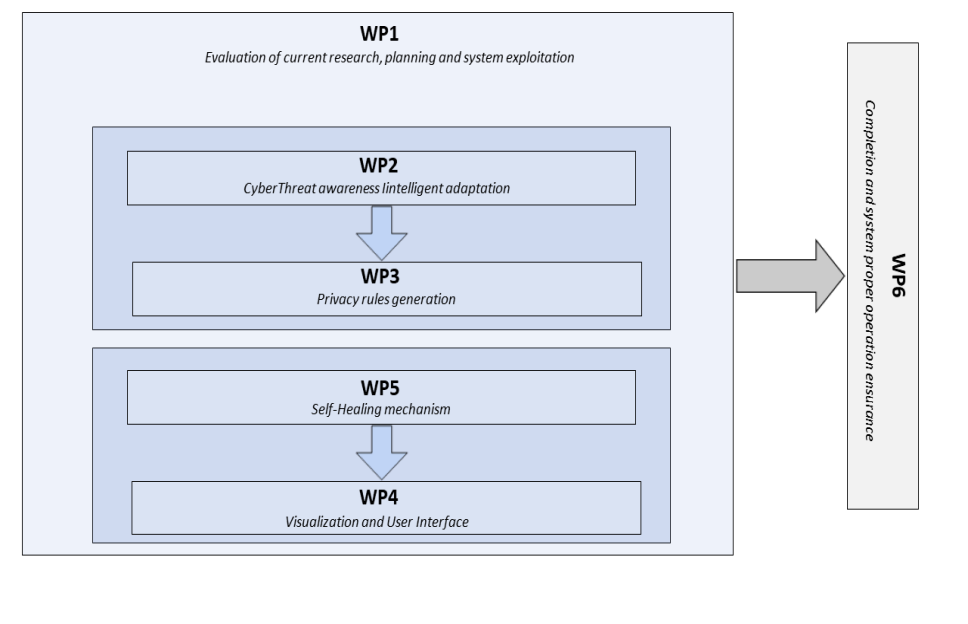
The project comprises six distinct work packages
Objectives
- Listing current technological research.
- Modeling business functions and specific characteristics of the organization.
- Definition of the architecture and the specifications of the system.
- Dissemination and utilization of produced research.
WP1 focuses on searching and reviewing relevant bibliography for defining the current technological research and to pinpoint the parts of this research that are to be further researched and expanded. Specifically, the current state of obtaining cyber threat intelligence (e.g. STIX, TAXII) and the evaluation methods of the sources of serving it will be studied. Reconnaissance and logging of the business functions of the pilot application as well as its specific characteristics (technological environment, personnel) will take place so as to be served with intelligence related to its specificity. The system architecture and specifications that will constitute the reference point for the rest of the work packages will be defined. Finally, a webpage for the dissemination and of the research results of the project and a plan for its future commercial exploitation will be created after it is completed.
Deliverables
- D1.1-Description of the current state (M4)
- D1.2-Description of system architecture and specifications (M6)
- D1.3-Creation of a webpage to disseminate the project research (M6)
- D1.4-Commercial capitalization plan (M26)
- D1.5-A publication in a scientific journal or conference (M12)
Objectives
- Evaluation and selection of cyber threat intelligence sources.
- Modeling and development of cyber threat intelligence adaptation subsystem based on the specific characteristics of the organization.
WP2 focuses on the development of the intelligent mechanism that will gather and filter cyber threat intelligence based on the organization systems. Primarily, publicly available sources for intelligence acquisition will be used. Sources will be evaluated according to the quality of the supplied intelligence (e.g. MISP, Hail-a-TAXII). Filtering will be done by harnessing information resulted from WP1 in regards to business functions and specific characteristics of organizations.
Deliverables
- D2.1-Cyber Threat Intelligence Smart Adaptation mechanism (M22)
- D2.2-A publication in a scientific journal or conference (M22)
Objectives
- Creation of rules for detecting incidents regarding personal data.
In the context of WP3 a modeling of rules will be conducted (e.g. through the usage of SIGMA language). These rules will be used by the detection system to execute automated personal data breach detection. To this end, the adaptive cyber threat intelligence produced in WP2 will be utilized (e.g. a set of known malign IP addresses). Furthermore, the specific characteristics of the organization, as produced by WP1, will be put into use.
Deliverables
- D3.1-Privacy Rules Production mechanism (M22)
- D3.2-A publication in a scientific journal or conference (M22)
Objectives
- Development of a proper user interface for visualizing information.
- Development of a mobile application.
WP4 revolves around the development of the user interface through which the required information will be visualized (with the form of graphs and accompanying text or numbers). This way, user obtains instant access to information for the current state of personal data security his/her organization holds, possible incidents that were detected and need further investigation, as well as possible imminent threats. Moreover, a relevant mobile application will be developed which will allow the user to have access to the aforementioned information through his/her mobile phone. Finally, an approach method for raising the level of awareness for cyber threats against privacy through visualization will be developed.
Deliverables
- D4.1-Information visualization platform and user interface (M22).
- D4.2-Mobile application (M22)
- D4.3-A publication in a scientific journal or conference (M22)
Objectives
- Development of Automated Threat and Attack Management Subsystem.
- Development of policies for automated communication with security mechanisms.
WP5 deals with the development of a threat and attack management mechanism which will automatically interfere in a specified set of security mechanisms (e.g. firewalls) to protect the organization from detected threats, either preemptively or suppressively, whenever the detection mechanism detects a threat. For the part of the automated decision making appropriate reaction policies will be developed for countering or containing attacks.
Deliverables
- D5.1-Automated Threat and Attack Management mechanism (M20)
- D5.2-A publication in a scientific journal or conference (M20)
Objectives
- Completion and proper function evaluation.
- Pilot application in two different use case scenarios and result assessment.
- Documentation manual creation.
WP6 focuses on the integration of the existing cyber threat detection system (OSSEC) into the subsystems developed in WP2-WP5 to result in the final product with enriched functionality. Afterwards, the system will be checked for proper functionality, the validity of the results it produces and it will be pilot deployed in two organizations with different and distinct qualitative characteristics. Finally, the compilation of a manual will commence with the goal of providing to the end user all the necessary information regarding the system functionality.
Deliverables
- D6.1-Completion and evaluation report of the final system (M30)
- D6.2-Pilot use case deployment report (M30)
- D6.3-User manual (M30)
- D6.4-A publication in a scientific journal or conference (M30)




